Securely Connect Remote IoT VPC Raspberry Pi: Free Download Guide
Connecting a Raspberry Pi to a remote IoT VPC securely has become a critical task for developers and enthusiasts alike. As the Internet of Things (IoT) continues to grow, the need for robust security measures and efficient connectivity solutions becomes increasingly important. This article will guide you step-by-step on how to securely connect your Raspberry Pi to a remote VPC while ensuring data privacy and protection.
In today's interconnected world, IoT devices are becoming an integral part of both personal and professional environments. From smart homes to industrial automation, the potential applications of IoT are limitless. However, with great power comes great responsibility. Ensuring secure communication between devices is essential to protect sensitive information and maintain system integrity.
This comprehensive guide will explore the tools, techniques, and best practices for securely connecting your Raspberry Pi to a remote VPC. Whether you're a beginner or an experienced developer, this article will equip you with the knowledge and resources to implement a secure IoT setup. Let's dive in!
Read also:Emmy Clarke 2021 Rising Star In The Entertainment Industry
Table of Contents
- Introduction to Secure IoT Connections
- Understanding Raspberry Pi Basics
- What is a Virtual Private Cloud (VPC)?
- Methods for Securely Connecting IoT Devices
- Essential Tools and Software
- Step-by-Step Guide to Secure Connection
- Common Issues and Troubleshooting
- Best Practices for IoT Security
- Free Download Resources
- Conclusion and Call to Action
Introduction to Secure IoT Connections
IoT devices are revolutionizing the way we interact with technology. However, the security challenges associated with these devices cannot be overlooked. A secure connection ensures that data transmitted between devices remains private and protected from unauthorized access. This section will delve into the importance of secure IoT connections and why they matter in today's digital landscape.
Why Security Matters in IoT
IoT devices often handle sensitive information, such as personal data, financial transactions, and critical infrastructure controls. Without proper security measures, these devices can become vulnerable to cyberattacks, leading to data breaches and system failures. By securing your IoT setup, you can safeguard your assets and maintain trust with users.
Understanding Raspberry Pi Basics
The Raspberry Pi is a versatile single-board computer that has gained immense popularity among hobbyists and professionals alike. Its affordability, flexibility, and ease of use make it an ideal platform for IoT projects. In this section, we will explore the fundamental aspects of Raspberry Pi and its role in IoT applications.
Key Features of Raspberry Pi
- Compact and lightweight design
- Support for multiple operating systems
- GPIO pins for interfacing with external devices
- Low power consumption
What is a Virtual Private Cloud (VPC)?
A Virtual Private Cloud (VPC) is a secure and isolated network environment within the cloud. It allows you to deploy and manage resources while maintaining control over network configurations and security settings. Understanding VPCs is crucial for setting up a secure IoT infrastructure.
Benefits of Using a VPC
VPCs offer several advantages, including:
- Enhanced security through network isolation
- Customizable network configurations
- Scalability to accommodate growing demands
- Integration with other cloud services
Methods for Securely Connecting IoT Devices
There are various methods to securely connect IoT devices to a remote VPC. Each method has its own set of advantages and considerations. In this section, we will discuss the most common and effective approaches.
Read also:Chaol Westfall The Ultimate Guide To His Life Character And Legacy
1. SSH Tunneling
SSH (Secure Shell) tunneling is a popular method for establishing secure connections between devices. It encrypts data transmitted over the network, ensuring privacy and protection from eavesdropping.
2. SSL/TLS Encryption
SSL/TLS encryption is widely used for securing communication between web servers and clients. It provides end-to-end encryption, making it ideal for IoT applications.
3. Virtual Private Network (VPN)
A VPN creates a secure and encrypted connection between devices, making it an excellent choice for remote IoT setups. It allows devices to communicate as if they were on the same local network, regardless of their physical location.
Essential Tools and Software
To securely connect your Raspberry Pi to a remote VPC, you will need the right tools and software. This section will highlight the essential components required for a successful setup.
Software Recommendations
- OpenSSH for SSH tunneling
- OpenVPN for secure VPN connections
- MQTT for lightweight IoT communication
Hardware Requirements
Ensure your Raspberry Pi is equipped with the necessary hardware components, such as:
- A stable power supply
- A reliable internet connection
- External storage for additional capacity
Step-by-Step Guide to Secure Connection
This section will provide a detailed step-by-step guide to securely connect your Raspberry Pi to a remote VPC. Follow these instructions carefully to ensure a successful setup.
Step 1: Configure Raspberry Pi
Begin by setting up your Raspberry Pi with the latest version of Raspberry Pi OS. Update the system and install any required software packages.
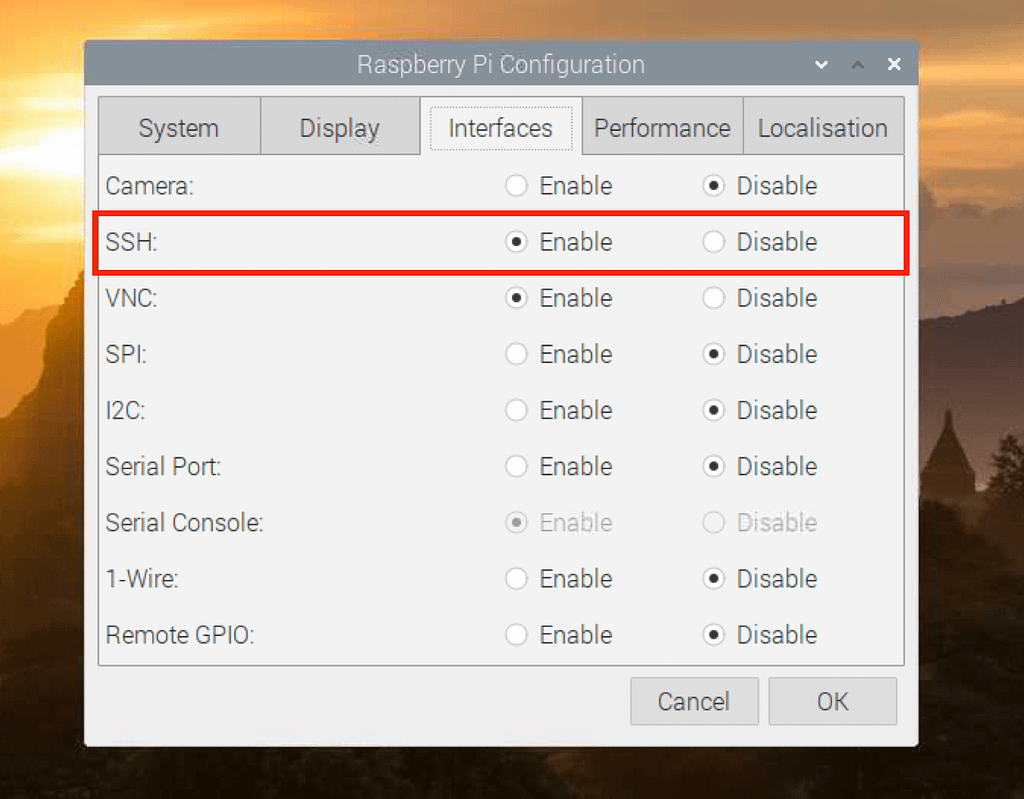
Step 2: Set Up SSH
Enable SSH on your Raspberry Pi and generate SSH keys for secure authentication. Use these keys to establish a secure connection to your VPC.
Step 3: Configure VPC
Create a VPC in your preferred cloud provider and configure the necessary security groups and access controls. Ensure that only authorized devices can access the VPC.
Step 4: Establish Secure Connection
Use SSH tunneling or a VPN to establish a secure connection between your Raspberry Pi and the VPC. Test the connection to ensure it is functioning properly.
Common Issues and Troubleshooting
Even with careful planning, issues may arise during the setup process. This section will address common problems and provide solutions to help you troubleshoot effectively.
Troubleshooting Tips
- Check network configurations for errors
- Verify SSH keys and authentication settings
- Test the connection using diagnostic tools
Best Practices for IoT Security
To ensure the long-term security of your IoT setup, it is essential to follow best practices. This section will outline key strategies for maintaining a secure IoT environment.
Regular Updates
Keep your software and firmware up to date to protect against vulnerabilities and exploits.
Strong Authentication
Implement strong authentication mechanisms, such as multi-factor authentication, to enhance security.
Monitor and Audit
Regularly monitor your IoT devices and network for suspicious activity. Conduct audits to identify and address potential security risks.
Free Download Resources
For your convenience, we have compiled a list of free resources to help you with your Raspberry Pi and IoT projects. These resources include software, documentation, and tutorials.
Recommended Downloads
- Raspberry Pi OS
- OpenSSH
- OpenVPN
Conclusion and Call to Action
In conclusion, securely connecting your Raspberry Pi to a remote IoT VPC is a critical step in building a robust and reliable IoT setup. By following the guidelines and best practices outlined in this article, you can ensure the security and integrity of your IoT infrastructure.
We encourage you to share your thoughts and experiences in the comments section below. Additionally, feel free to explore other articles on our website for more insights into IoT and related technologies. Together, let's build a safer and more connected world!
References: